
Mid-Week Market Minute 4.17.24
Inflation concerns overshadowed a relatively upbeat start to earnings season with stocks trending lower. The Fed Chair weighed in on market sentiment on Tuesday, highlighting the lack of progress on inflation so far this year. Earnings reports will remain at the forefront over the next several weeks.
Read More
Market Recap – Week Ending April 12
The S&P 500 fell 1.5% last week, its worst week since October, after the U.S. Consumer Price Index (CPI) rose 0.36% in March and 3.48% over the prior year. JPMorgan Chase, Citigroup, and Wells Fargo all kicked of first-quarter earnings results with strong revenues and earnings beats.
Read More
Mid-Week Market Minute 4.10.24
As of Wednesday morning, the S&P 500 was lower by about 1% on the week while the more interest-rate sensitive Russell 2000 (small cap index) was lower by about 2% after the March CPI report showed prices accelerated more quickly than expected. From the Fed’s vantage point, the inflation report likely means a June rate cut is off the table.
Read More
Market Recap – Week Ending April 5
After ending the first quarter with more than a 10% gain, the S&P 500 index recorded its biggest weekly loss since early January, down 0.9%. Markets ended the week on a positive note with the above-consensus jobs report on Friday. The March consumer (CPI) and producer (PPI) prices reports are due out Wednesday and Thursday, respectively.
Read More
Mid-Week Market Minute 4.3.24
The S&P 500 is lower by a little more than 1% while the Russell 2000 was lower by more than 2.5% at the halfway point this week. The S&P 500 achieved 22 new all-time highs in the first quarter of this year. Markets will pay close attention to the non-farm payrolls report, which will be released Friday.
Read More
Mid-Week Market Minute 3.27.24
Major indices are on pace to finish the month higher with the S&P 500 set to finish March a little more than 2% higher. Thursday’s final reading of Q4 2023 real GDP growth is expected to remain unchanged from last month’s estimate of 3.2%, while Friday’s release of the Core PCE Price index is expected to show inflation at around 2.8% year-over-year.
Read More
Market Recap – Week Ending March 22
The S&P 500 index finished the week higher by 2.3% and the Nasdaq Composite rose 2.9% as markets are on track for a fifth consecutive month of positive returns. Fed data showed an expectation of three rate cuts over the course of the year. The next PCE Price Index, the Fed’s preferred inflation gauge, will be released Friday.
Read More
Mid-Week Market Minute 3.20.24
While stocks were higher in early trading this week, markets will look at what comes out of the Federal Reserve meeting ending Wednesday. No change is expected for interest rates at the meeting. Intel was awarded more than $8 billion in CHIPS Act funding, the initiative to bring semiconductor manufacturing to the U.S.
Read More
Market Recap – Week Ending March 15
Inflation concerns have pressured stocks recently, with recent reports adding to concerns the Federal Reserve may wait longer before considering cutting interest rates. The next Federal Reserve policy meeting is this week, March 19-20, where markets will receive updated growth and interest-rate projections from Fed members.
Read More
Mid-Week Market Minute 3.13.24
On Tuesday, the S&P 500 index closed at a record high for the 17th time this year. The monthly jobs report and resilient consumer spending have aided the outlook for economic growth. Economists expect the U.S. economy to grow at an annualized rate of 1.8% in the first quarter, up from projections for 0.6% in January, according to Bloomberg data.
Read More
Married Filing Student Loans
Isn’t the box you check when filing determined by your marital status? What else is there to think about? For married couples with federal student loans, the tax-filing status selection and repayment option may impact student loan payments.
Read More
Market Recap – Week Ending March 8
The S&P 500 and Nasdaq Composite fell back slightly at week’s end while small cap stocks managed a positive week. The nonfarm payrolls jobs report showed the U.S. economy added 275,000 jobs, above expectations. Key inflation data releases this week include the Consumer Price Index (CPI) on Tuesday and the Producer Prices Index (PPI) on Thursday.
Read More
SECURE 2.0: A win-win for small businesses, employees and forward-thinking advisors
The new law bolsters small businesses' ability to provide retirement benefits to their employees by offering tax credits to offset costs; however, for advisors, it's an unprecedented opportunity to tap into a new revenue stream.
Read More
Mid-Week Market Minute 3.6.24
The S&P 500 was lower by about 0.50% on the week, while the Russell 200 was about 1% lower. In prepared remarks for appearances on Capitol Hill, the Fed Chair hinted rate cuts still were likely this year but cautioned of reducing policy constraints too early. The widely followed jobs report will be released Friday.
Read More
Emotional Investing: Overcoming the Challenges
As every seasoned financial professional knows, the type and intensity of emotions tied to financial beliefs and actions are different for everyone. But one recurring source of emotional stress that seems inescapable is election season.
Read More
Changing Jobs? What To Do With Your Old 401(k)
Amid the chaos of a job change, there’s one task that often falls through the cracks: remembering your 401(k) with your previous employer. In fact, based on research by Capitalize, 1 in 5 U.S workers have forgotten or left behind a 401(k) plan when changing jobs.
Read More
Market Recap – Week Ending March 1
The Nasdaq index reached an all-time high last Friday while the S&P 500 index, up 1.0%, has recorded gains in seven of the last eight weeks as declining inflation, positive sentiment in artificial intelligence, and strong quarterly earnings have fueled recent market enthusiasm. Fed Chair Jerome Powell will provide policy updates to Congress this week.
Read More
Mid-Week Market Minute 2.28.24
The S&P 500 was lower by about 0.50%, while the Russell 2000 (small cap index) was higher by nearly 2% this week. On Thursday, the PCE report, the Federal Reserve’s preferred measure of inflation, will be released and is expected to show the rate of inflation accelerated month-over-month for both the headline and core indices, while year-over-year inflation is expected to decelerate.
Read More
Market Recap – Week Ending Feb. 23
The S&P 500 finished the week higher by 1.7%, while international developed (MSCI EAFE) and emerging markets (MSCI EM) notched similar gains. Minutes from the January FOMC meeting showed Fed members remain sensitive to inflationary risks and expressed a tone of patience in delivering future rate cuts. In economic data, manufacturing data (PMI) showed strength in January.
Read More
Mid-Week Market Minute 2.21.24
Walmart reported double-digit growth in e-commerce sales while Home Depot beat earnings and revenue estimates. The Federal Reserve will release minutes from the January meeting as futures markets now project 3-4 rate cuts this year. Mortgage applications fell 10.6% last week; existing home sales data later this week.
Read More
Market Recap – Week Ending Feb. 16
Emerging markets (MSCI EM) and international developed (MSCI EAFE) posted positive returns, while the S&P 500 index had to rebound to finish the week just 0.4% lower. It saw its worst one-day drop in more than a year, triggered by a high-than-consensus CPI report. Walmart, Home Depot and tech giant Nvidia earnings reports are due this week.
Read More
Mid-Week Market Minute 2.14.24
The S&P 500 index was down about 1% mid-week, while the more interest-rate sensitive Russell 2000 was about 2% lower. Tuesday’s CPI report showed headline inflation rising at a 3.1% annual clip with core inflation higher by 3.9%, both higher than projections. Thursday will see the release of retail sales data and the next GDP estimate.
Read More
Market Recap – Week Ending Feb. 9
The S&P 500 index finished last week 1.4% higher as stocks extended their global rally. As of Feb. 9, 67% of the S&P 500 have announced 2023 fourth-quarter earnings with 75% reporting earnings above consensus expectations. The Consumer Price Index (CPI) is due Tuesday with headline CPI expected to fall to 3.0% on a year-over-year basis.
Read More
Mid-Week Market Minute 2.7.24
Stocks are mixed this week as investors weighed commentary from Fed officials alongside ongoing corporate earnings results. Following the FOMC policy announcement last week and related commentary, the probability of a rate cut at the March meeting has fallen to less than 25%. The January CPI report will be released next week.
Read More
Market Recap – Week Ending Feb. 2
The S&P 500 index rose 1.4% last week as U.S. stocks were higher for the 13th of the last 14 weeks. Big tech reported strong earnings while the January jobs report showed the highest month of job creation in 12 months. As the latest Federal Reserve meeting concluded, Fed Chair Jerome Powell indicated March may be too early to begin rate cuts.
Read More
Mid-Week Market Minute 1.31.24
The S&P 500 was on pace to notch its third consecutive month of positive returns as of Wednesday morning. Microsoft and Alphabet beat fourth-quarter earnings expectations; Apple, Facebook, and Amazon reports coming later this week. Markets are waiting to hear from the Federal Reserve following the central bank’s policy announcement on Wednesday afternoon.
Read More
Market Recap – Week Ending Jan. 26
The S&P 500 index was higher by 1.1%, aided by strong economic growth and encouraging inflation data. Core PCE fell to 2.9% year-over-year, the lowest level since March 2021. This week, 109 of the S&P 500 companies are scheduled to report fourth-quarter earnings, including Microsoft, Apple, Facebook, Google, and Amazon.
Read More
Mid-Week Market Minute 1.24.24
Tech stocks led the way as the S&P 500 and Dow Jones Industrial Average both reached new all-time highs. International stocks also moved higher this week. The first estimate of fourth quarter GDP is due Thursday with the Fed’s preferred inflation measure, the PCE deflator, coming on Friday.
Read More
Market Recap – Week Ending Jan. 19
While stocks across the world were mixed, the S&P 500 index ended the week up 1.2% to reach an all-time high. The 2-Year and 10-Year Treasury yields ended last week higher at 4.41% and 4.14%, respectively. The 2023 fourth-quarter GDP comes out Thursday and the personal consumption expenditures (PCE) will be reported Friday.
Read More
Mid-Week Market Minute 1.17.24
December retail sales surpassed expectations, rising 0.6% against the anticipated 0.4% gain. Industrial production also exceeded consensus. Futures markets now indicate a 60% chance the Fed will cut rates at their March 20 meeting. Fourth-quarter earnings gain momentum this week.
Read More
Is My Client Being Scammed?
Scammers may manipulate clients into withdrawing funds from their investment accounts. As their trusted Financial Professional, you should closely review and question requests that seem sudden or unusual.
Read More
Market Recap – Week Ending Jan. 12
The S&P 500 index was up 1.9% for the week, the 10th of last 11 weeks it has finished higher. The December CPI report showed inflation increased more than expected, driven largely by shelter costs, car insurance and hospitality increases. On the data front, retail sales are due Wednesday, and several major banks will release earnings this week.
Read More
Bond Portfolios vs. Cash – Long-term Investors Should Own Bonds
In this recent market, where short-term yields are the same or higher than long-term yields, some investors have replaced model bond portfolios with cash. Many are questioning the role of fixed income when cash can yield the same amount or more.
Read More
Mid-Week Market Minute 1.10.24
After a broad-based rally Monday, stocks digested the positive trade mid-week as investors await key inflation data. Consumer Price Index (CPI) and producer prices (PPI) for December are due this week. Fourth-quarter 2023 earnings season gears up Friday.
Read More
Market Recap – Week Ending Jan. 5
The S&P 500 index finished the week down 1.5% and stocks across the globe started 2024 lower. Investors will look for clues on inflation with the releases of the December CPI and PPI this week, with core CPI expected to fall to 3.8% on a year-over-year basis. The latest earnings season will kick off Friday.
Read More
Mid-Week Market Minute 1.3.24
Global stocks were marginally lower to start the week with the technology heavy Nasdaq index down more than 1.5% on Tuesday. This week, key data releases include manufacturing and employment, and minutes from the latest FOMC meeting. The next Fed meeting is Jan. 31.
Read More
Market Recap – Week Ending Dec. 29
Emerging markets (MSCI EM) were up 3.3% to lead the way while the S&P 500 index rose 0.3% to notch its eighth consecutive week of gains to close out 2023. The Core personal consumption index (Core PCE) decreased to 3.2% in November, beating consensus expectations. Key jobs data will be released on Friday, Jan. 5.
Read More
Boost your tax practice's bottom line with a wealth manager
Tax professionals (including CPA, Enrolled Agents and others) and financial advisors play critical roles in guiding their clients through complex financial matters. Whether it's managing and optimizing tax efficiency or creating comprehensive financial plans, these highly trusted professionals bring immense value to their clients' financial lives.
Read More
Market Recap - Week Ending Dec. 15
The S&P 500 index rallied more than 2.5%, while the Dow Jones Industrial Average reached a new all-time high. Lower interest rates continue to be the primary catalyst behind this relentless rally.
Read More
Mid-Week Market Minute 12.13.23
Domestic and international stocks have staged an impressive rally over the past several weeks on the back of lower interest rates and optimism surrounding a potential soft-landing for the economy. November CPI inflation came in as expected with core inflation gaining 4.0% on an annual basis.
Read More
Market Recap – Week Ending Dec. 8
Stocks were little changed last week ahead of the final Federal Reserve meeting of 2023 this week. While labor market data was mixed last week, this week will see the release of important inflation data reports, including consumer prices (CPI) on Tuesday, producer prices (PPI) on Wednesday and retail sales data on Thursday.
Read More
Mid-Week Market Minute 12.6.23
In early trading this week, global stocks were mostly flat and the yield on the 10-year Treasury note briefly dropped below 4.20% on Tuesday. Job openings figures for October came in well below the consensus while the S&P Global US Composite PMI showed an economy that is slowly expanding.
Read More
Market Recap – Week Ending Dec. 1
Stocks traded higher for the fifth consecutive week with the S&P 500 Index closing at a new 2023 high on Friday, up 0.8% for the week and more than 21% year-to-date. The Russell 2000 Index was higher by more than 3%. Key data this week will come on Friday, the monthly employment report.
Read More
Upcoming Tax Changes: Implications on Tax Returns and Financial Planning
Recent legislation underscores the importance of integrating tax planning with investment and retirement planning to maximize clients’ financial opportunities.
Read More
Mid-Week Market Minute 11.29.23
Stocks were unchanged in early trading this week, but on pace to finish November markedly higher, led by international developed stocks up more than 9% this month. On Thursday, the PCE inflation report will be released with both headline and core prices expected to decline.
Read More
Market Recap – Week Ending Nov. 24
The S&P 500 index was up 1.0%, notching gains for the fourth consecutive week, as international and domestic stocks have recorded strong performances in November. The October Personal Consumption Expenditures (PCE) Index will be reported Thursday.
Read More
Mid-Week Market Minute 11.22.23
Both large cap stocks (S&P 500 index) and the small cap index (Rusell 2000) are up around 8% for the month as stocks continued to rally in this holiday-shortened week. As economic data shows the labor market losing momentum, the Fed’s latest minutes show it will take a cautious approach to rates and will continue to evaluate incoming data.
Read More
Market Recap – Week Ending Nov. 17
The S&P 500 index ended the week 2.3% higher, it’s third consecutive week of gains, and the MSCI EAFE (4.5%) and MSCI EM (3.0%) both were higher for the week. Economic data will be light this week, highlighted by home sales data on Tuesday and durable goods orders on Wednesday.
Read More
Mid-Week Market Minute 11.15.23
In early trading this week, the S&P 500 climbed nearly 2% while the Russell 2000 jumped by more than 5% after Tuesday’s CPI report showed headline and core inflation were higher by 3.2% and 4.0%, respectively, for October. Wednesday’s PPI report confirmed the disinflationary trends, falling 0.5% in October against expectations for a 0.1% increase.
Read More
Market Recap – Week Ending Nov. 10
The S&P 500 rose more than 1% while the technology-heavy Nasdaq index rallied more than 2%. Moody’s lowered its U.S. credit rating to negative, citing fiscal deficits and political division as key factors, amid a resurging threat of a U.S. government shutdown. Tuesday will bring the widely followed CPI inflation report.
Read More
Mid-Week Market Minute 11.08.23
The S&P 500 notched its eighth consecutive day of positive returns on Tuesday. The recent rally comes on the heels of relatively strong third-quarter earnings results, which are on pace to grow by nearly 4% on a year-over-year basis, and lower interest rates. Next week, markets will be focused on CPI and Core CPI inflation due on Tuesday.
Read More
Market Recap – Week Ending Nov. 3
The Federal Reserve kept the rates the same at the end of their November meeting and jobs reports came in less than expected. Major stock indices in the U.S. responded with their best week of 2023 so far, with the S&P 500 index (5.9%) and the Nasdaq Composite (6.6%) both up.
Read More
Mid-Week Market Minute 11.01.23
The S&P 500 index was down about 2.2% in October as major indices are coming off a third-consecutive losing month. As of Oct. 27, about half of the companies in the S&P 500 have reported third-quarter 2023 earnings and 78% have exceeded earnings expectations. The Treasury Department announced it will increase the size of its note and bond auctions.
Read More
Market Recap – Week Ending Oct. 27
The S&P 500 now is down by 10.6% from its 2023 high and off about 4% month-to-date in October. Economic data showed core personal consumption declined to 3.7%, while initial estimate of GDP rose to 4.9% annualized in the third quarter. Another busy earnings week is ahead, including Apple on Thursday, and the monthly employment report is due Friday.
Read More
Mid-Week Market Minute 10.25.23
It’s been a mixed bag in the early stages for Q3 corporate earnings reports. Key economic releases include the first estimate of third-quarter GDP on Thursday and the PCE Price Index, the Fed’s preferred measure of inflation, on Friday.
Read More
Market Recap – Week Ending Oct. 20
Both U.S. and international stocks were lower on the week with the S&P 500 index snapping a three-week streak of gains, ending the week 2.4% lower. The first estimate of third-quarter GDP growth and earnings from tech giants Amazon, Meta, and Microsoft, among others, are due out this week.
Read More
Mid-Week Market Minute 10.18.23
The S&P 500 is up about 0.50% with the Russell 2000 higher by more than 2% this week. September retail sales rose 0.7% against forecasts for a 0.3% increase. Early earnings reports have been better than expected and will be closely followed in the coming days.
Read More
Market Recap – Week Ending Oct. 13
The S&P 500 index up by 0.47% and the MSCI EAFE was up about 1% to finish the week. Earnings reports this week will give investors a look at the health of the big banks, airlines, and media companies, among others. Analysts expect third-quarter earnings to show year-over-year growth of around 1.3%.
Read More
Mid-Week Market Minute 10.11.23
Stocks rallied early this week while Treasury yields retreated from 16-year highs. The September Producer Price Index (PPI) increased 0.5%, against expectations of a more moderate 0.3% increase. CPI report will be released Thursday morning.
Read More
Market Recap – Week Ending Oct. 6
U.S. stocks finished the week higher with the S&P 500 index up by 0.5%. Interest rates have trended higher with expectations that the Fed will keep rates higher-for-longer. Key inflation data will be reported on Thursday this week.
Read More
Mid-Week Market Minute 10.4.23
Treasury yields reached their highest levels since 2007 with higher interest rates the primary driver behind the recent market struggles. Mortgage demand hit its lowest point since 1996. Bureau of Labor’s nonfarm payrolls report is due out Friday, Oct. 6.
Read More
Market Recap - Week Ended Sept. 29
Congress passed a short-term funding bill and avoided a shutdown. The S&P 500 index was down 0.7% for the week, finishing its worst month of the year. The PCE Price Index decline reflects a slowing improvement of inflation.
Read More
Mid-Week Market Minute 9.27.23
For September, the S&P 500 is on pace to finish lower by nearly 5% with stocks in the energy sector are on pace to be the lone gainer. New home sales and consumer confidence data this week missed consensus estimates though durable goods orders for August came in stronger than expected.
Read More
Market Recap – Week Ending Sept. 22
The S&P 500 index was lower by 2.9% on the week and now is down about 4% for September. Markets now turning to concerns over a possible government shutdown Oct. 1. The PCE Price Index, the Fed’s preferred measure of inflation, comes out Friday.
Read More
Mid-Week Market Minute 9.20.23
The Federal Reserve is widely expected to announce a pause in rate increases at today’s news conference at 1:30 p.m. Central and markets will look for signs into the future path of Fed policy. Housing starts came in well below expectations but a jump in permits reflects optimism.
Read More
Market Recap – Week Ending Sept. 15
International developed stocks were slightly higher while the S&P 500 index finished lower by 0.1% last week. The Federal Reserve is widely expected to leave interest rates unchanged when its meeting concludes on Wednesday, Sept. 20.
Read More
Mid-Week Market Minute 9.13.23
The S&P 500 was higher by about 0.50% mid-week. August CPI inflation showed core inflation (excludes food and energy) at 4.3% and headline prices up 0.6% (3.7% increase on annual basis) with oil prices the primary driver.
Read More
Market Recap – Week Ending Sept. 8
The S&P 500 index and international developed stocks (MSCI EAFE) both were about 1% lower last week. Key reports this week include the Consumer Price Index (CPI) on Wednesday and retail sales data on Thursday.
Read More
Mid-Week Market Minute 9.06.23
Global stocks traded lower this week with the S&P 500 down about 1%, the Russell 2000 (small cap index) falling about 2% and the MSCI EAFE declined by about 1%. The Federal Reserve is expected to keep rates unchanged at the Sept. 19-20 meeting.
Read More
Market Recap – Week Ending Sept. 1
Last week, the S&P 500 index recorded its best weekly return since June as inflation data showed the smallest monthly gain in more than two years, supporting investor expectations the Federal Reserve will hold rates steady at the upcoming Sept. 20 meeting.
Read More
Mid-Week Market Minute 8.30.23
The S&P 500 (total return) was higher by nearly 2.3% as of mid-week. The second estimate of Q2 real GDP came in lower than expected at 2.1% on an annualized basis. PCE Price Index, monthly employment report later this week.
Read More
Market Recap – Week Ending Aug. 25
The S&P 500 rose for the first time in four weeks and finished the week higher by 0.8%. The Federal Reserve Chair, speaking at last week’s economic symposium, said the Fed’s job remains bringing inflation down to two percent.
Read More
Mid-Week Market Minute 8.23.23
After a significant pullback during the first half of the month, stocks ticked higher in early trading this week. The Fed’s GDPnow model projects real GDP to increase by more than 5% in the third quarter.
Read More
Market Recap – Week ending Aug. 18
As stocks were lower across the globe last week following disappointing economic data in China, strong economic data have market participants concerned the Federal Reserve may still need to hike rates to tame inflation.
Read More
Mid-Week Market Minute 8.16.23
The S&P 500 was down about 0.60% and international stocks were lower by about 1% in early trading this week. Consumers continue to show resiliency as retail sales came in well above consensus. Core retail sales increased 1% in July.
Read More
Market Recap – Week ending Aug. 11
The S&P 500 was down 0.3% as interest rates rose with 2-year and 10-year Treasury notes at 4.89% and 4.17%, respectively, last week. The CPI report showed continued disinflation, with headline, core consumer prices below consensus expectations.
Read More
Mid-Week Market Minute 8.9.23
Stocks were largely unchanged in early trading this week. With more than 80% of companies in the S&P 500 already have reported second-quarter results, overall earnings are on pace to perform better than expected. The CPI report for July will be released Thursday.
Read More
Market Recap – Week ending Aug. 4
Global stocks were lower last week as markets reacted to the downgrade of the U.S. long-term credit rating by Fitch. The S&P 500 ended its three-week streak of positive returns, finishing the week 2.3% lower. The July CPI report will be released Thursday.
Read More
Mid-Week Market Minute 8.2.23
Fitch downgrades U.S. long-term default rating for the U.S. Earnings and labor reports due this week. Second-quarter earnings season is more than halfway through with results coming in generally stronger than expected.
Read More
Market Recap - Week Ending 7.28.23
While the Federal Reserve hiked interest rates by 25bps, as expected, the S&P 500 index finished 1.0% higher as markets rallied on better-than-expected earnings and a strong GDP report. On the inflation front, the core PCE Index fell to 4.1% in June.
Read More
Mid-Week Market Minute 7.26.23
As investors digest second-quarter earnings results, stocks moved higher. Key releases this week on the economic data front are the first estimate of second-quarter GDP on Thursday and PCE Price Index on Friday.
Read More
Market Recap - Week Ending 7.21.23
International developed stocks and emerging markets fell slightly while S&P 500 index was up 0.7% last week. Markets expect Federal Reserve to announce a 0.25% rate hike on Wednesday. GDP, PCE Price Index data coming this week.
Read More
Mid-Week Market Minute 7.19.23
For July, all major indices are firmly in positive territory with the S&P 500 higher by about 2.5%. With the Fed approaching the end of its rate-hiking campaign, Q2 corporate earnings will be a focus the next few weeks.
Read More
Market Recap – Week ending July 14
The S&P 500 index was up 2.4% as investors were encouraged as U.S. core CPI fell to 4.8% in June. Earnings reports from big financial institutions and from Tesla, Netflix, and United Airlines are out this week.
Read More
Mid-Week Market Minute 7.12.23
As of mid-week, the S&P 500 is about 1.5% higher and the Dow Jones Industrial rallied more than 2%. June’s CPI report showed headline inflation rose 3% year-over-year; core inflation fell to 4.8%, an encouraging print.
Read More
Market Recap – Week ending July 7
The S&P 500 index fell 1.1%, and higher yields across the Treasury curve led to negative returns for bonds. Wednesday’s CPI report will be a key data metric as the Fed determines the upcoming path for interest rates.
Read More
Mid-Week Market Minute 7.5.23
For 2023’s first half, global stocks were firmly in positive territory. The S&P 500 total return index now sits less than 5% from all-time highs. Jobs report and minutes from June’s Fed meeting due this week.
Read More
Market Recap – Week ending June 30
The S&P 500 index was up 2.4% last week. In inflation data, June’s PCE Price Index (personal consumption) was 3.8%, down from 4.4% in May. Real GDP growth was revised upward from 1.4% to 2.0%.
Read More
Mid-Week Market Minute 6.28.23
Broadly speaking, stocks on pace to post impressive gains for June, with the S&P 500 higher by nearly 5% as of June 28. Economic data showed consumer confidence and new home sales both above consensus expectations.
Read More
Market Recap – Week ending June 23
The S&P 500 index was down 1.4% as investors brace for potentially higher interest rates from the Federal Reserve. Key inflation data coming Friday includes headline PCE Price Index, the preferred inflation gauge for the Fed.
Read More
Mid-Week Market Minute 6.21.23
The S&P 500 was lower by about 1% in early trading this week. Mega-cap growth stocks in the U.S. having quite a year. Fed Chair noted FOMC participants expect to raise interest rates somewhat further by end of year.
Read More
Market Recap – Week ending June 16
The S&P 500 reached a new year-to-date high, finishing the week 2.6% higher. The Federal Reserve paused interest-rate hikes since their tightening cycle began 15 months ago. Economic data last week was encouraging.
Read More
Mid-Week Market Minute 6.14.23
In early trading this week, S&P 500 was higher by about 1.6%, while the Nasdaq Composite rallied another 2.4%. The May CPI report showed headline inflation rising just 0.1% with year-over-year prices up 4%.
Read More
Market Recap – Week ending June 9
Global stocks were higher with the S&P 500 slightly up. Consumer and producer data coming this week. Expectations are for the Federal Reserve to leave the funds rate unchanged at its meeting that ends Wednesday.
Read More
Mid-Week Market Minute 6.7.23
Stocks and bonds basically are unchanged for the week. Next week, the May CPI report will be released on Tuesday, and the Federal Reserve will meet June 13-14.
Read More
Market Recap – Week ending June 2
The S&P 500 index had its best performance since March, higher by 1.9%. strong jobs data and the passage of the bill to raise the debt ceiling helped buoy the markets.
Read More
Mid-Week Market Minute 5.31.23
Growth stocks and, more specifically, technology stocks, have significantly outperformed value stocks so far this year. Several data reports related to the labor market will be released this week.
Read More
Mid-Week Market Minute 5.24.23
While global stocks trended lower, Treasury bond yields moved higher as investors anxiously await a debt-ceiling resolution. GDP and PCE Price Index data due this week.
Read More
Market Recap – Week ending May 19
The S&P 500 index was higher by 1.7% and international stocks also finished in positive territory last week. With more than 90% of the S&P 500’s market cap having reported, profit margins currently stand at 11.8%.
Read More
Mid-Week Market Minute 5.17.23
While debt-ceiling talks showed progress, the parties remain apart on several key issues. April retail sales rose by 0.4%, less than expectations, though core retail sales jumped more than expected.
Read More
Market Recap – Week ending May 12
Earnings releases and debt-ceiling talks continue to influence market returns as the S&P 500 was down 0.2% last week. Reports on retail sales, industrial production, and housing are due this week.
Read More
Mid-Week Market Minute 5.10.23
April’s CPI report showed headline inflation rose 4.9% year-over-year, in line with market expectations. Elevated volatility in stocks, bonds is expected until debt ceiling situation is resolved.
Read More
Market Recap – Week ending May 5
The Federal Reserve delivered further interest-rate hikes last week and U.S. stocks finished the week lower. The CPI report is due Wednesday with expectations inflation will be modestly lower than last month.
Read More
Mid-Week Market Minute 5.3.23
The Federal Reserve announced a 0.25% increase in interest rates at the conclusion of its May meeting. The S&P 500 closed Wednesday about 2% lower on the week.
Read More
Market Recap – Week ending April 28
The Federal Reserve is expected to raise the fed funds rate by 0.25% (25bp) at this week’s meeting. Last week’s 1Q GDP report was below expectations, while consumption increased 3.7% over the first quarter.
Read More
Mid-Week Market Minute 4.26.23
First-quarter profits for Alphabet (Google) and Microsoft came in better than expected. Key releases this week include GDP for first quarter and PCE Price index, the Fed’s preferred measure of inflation.
Read More
Market Recap – Week ending April 21
Earnings reports continue with companies such as Alphabet, Meta, Amazon, and Microsoft to highlight a busy week. First-quarter GDP data is due Thursday, personal income and outlays data due Friday.
Read More
Mid-Week Market Minute 4.19.23
Stocks were mixed while interest rates for bonds were higher. U.S. housing demand is weakening. Investors are watching earnings reports to see if Fed’s efforts are affecting economic activity.
Read More
Market Recap – Week ending April 14
March CPI reported at 5.0% year-over-year, below consensus expectations. This earnings season, 90% of the companies reporting during the first week beat their first-quarter estimates.
Read More
Mid-Week Market Minute 4.12.23
U.S. stocks were mixed as March’s Consumer Price Index (CPI) showed prices increased 5% year over year. The Federal Reserve is expected to raise interest rates by another 0.25% in May.
Read More
Mid-Week Market Minute 4.5.23
The S&P 500 was slightly lower in trading this week while U.S. Treasury yields moved lower. The latest ADP private payrolls report showed slowing job growth.
Read More
Market Recap – Week ending Mar. 31
The volatile first quarter of 2023 ends in positive territory, with S&P 500 up 7.5%. February’s PCE, the Fed’s preferred measure of inflation, was 4.6% year-over-year, below consensus expectations.
Read More
Mid-Week Market Minute 3.29.23
The S&P 500 was higher by about 1% in trading this week; bond rates also were higher. The PCE price index, the Fed’s preferred measure of inflation, is due Friday.
Read More
Market Recap – Week ending Mar. 24
Federal Reserve, European banks made interest-rate hikes, but global stocks were up last week while bond yields remained volatile. PCE data expected to show signs inflation continuing to slow.
Read More
Mid-Week Market Minute 3.22.23
The Federal Reserve, as expected, raised interest rates by 0.25% (25bp) on Wednesday. The FOMC noted future increases will depend largely on incoming data.
Read More
Market Recap – Week ending Mar. 17
The S&P 500 index was 1.5% higher in volatile trade last week. Markets are pricing in about a 70% chance of a 25-basis-point hike at the Federal Reserve’s March 21-22 meeting.
Read More
Mid-Week Market Minute 3.15.23
Markets were volatile after recent banking news. On data front, CPI’s 6% rate in February met expectations; PPI (4.6%) was lower than expected. Federal Reserve meeting is next week.
Read More
Market Recap – Week ending Mar. 10
The S&P 500 index fell 4.5% last week, reacting to concerns in the banking system and remarks from Federal Reserve Chair Jerome Powell. Data shows labor market remains resilient.
Read More
Mid-Week Market Minute 3.8.23
Stocks were lower after Federal Reserve Chair Jerome Powell said economic data shows the ultimate level of interest rates is likely to be higher than previously anticipated.
Read More
Market Recap – Week ending Mar. 3
The S&P 500 snapped a streak of three consecutive down weeks. Key employment data due this week with ADP report on Wednesday and U.S. nonfarm payrolls report on Friday.
Read More
Mid-Week Market Minute 3.1.23
The Dow Jones Industrial Average and the S&P 500 were down about 4.2% and 2.6%, respectively, in February. Thursday brings the Job Openings and Labor Turnover report.
Read More
Market Recap – Week ending Feb. 24
Global and U.S. stocks fell last week as markets digested the minutes from February’s Federal Reserve meeting and the core PCE Price Index came in well above consensus expectations.
Read More
Mid-Week Market Minute 2.22.23
The S&P 500 was lower by about 2% on Tuesday, marking the worst day of 2023 thus far. The personal income and outlays report, a key release, is due Friday.
Read More
Market Recap – Week ending Feb. 17
Global stocks were largely unchanged last week as investors continue to decipher monetary policy and inflation. In the U.S., the S&P 500 index finished the week lower by 0.2%, but still is up 6.5% for the year.
Read More
Mid-Week Market Minute 2.15.23
The January CPI report showed hotter-than-expected inflation as stocks and bonds trended higher. The advance estimate of retail sales was stronger than expectations, showing a 3% jump.
Read More
Market Recap – Week Ending 02.10.23
Investors continued to evaluate the implications of monetary policy and mixed corporate earnings last week. The CPI report for January will be released Tuesday.
Read More
Mid-Week Market Minute 2.8.23
Stocks were relatively unchanged as investors digested corporate earnings and comments from Fed Chair Jerome Powell. Markets now are pricing in two additional 0.25% (25 basis point) interest rate hikes for the remainder of the year.
Read More
Market Recap – Week ending Feb. 3
The S&P 500 index was up 1.6% last week, a five-month high. Friday’s monthly employment report showed unemployment fell to 3.4%, the lowest level since 1969.
Read More
Mid-Week Market Minute 2.1.23
The S&P 500 posted its best January since 2019, while the NASDAQ recorded its best January in 22 years. Market heavyweights to report fourth-quarter earnings this week.
Read More
Market Recap – Week ending Jan. 27
Fourth-quarter U.S. GDP came in better than expected to boost stocks. This week, earnings reports are due from key companies, and Fed is expected to raise the funds rate by 0.25% (25bp).
Read More
Mid-Week Market Minute 1.25.23
Markets mixed after latest batch of corporate earnings reports. Personal consumption expenditure (PCE), a key inflation gauge for the Fed, and GDP data coming this week.
Read More
Market Recap – Week ending Jan. 20
The S&P 500 finished the week slightly lower, while bonds continued their strong run. Key economic reports and earnings from several market heavyweights are due this week.
Read More
Mid-Week Market Minute 1.18.23
Earnings reports from banks were mixed this week. Inflation data shows declining prices while retail sales fell more than expected.
Read More
Market Recap – Week ending Jan. 13
The S&P 500 index rose 2.7% as investors were encouraged by indications of declining inflation. Key economic data, including a large calendar of earnings, are due this week.
Read More
Mid-Week Market Minute 1.11.23
Technology and communications stocks were notably higher as the Nasdaq composite index rallied nearly 2%. Markets are looking toward Thursday’s CPI inflation report.
Read More
Market Recap – Week ending Jan. 6
Positive returns last week for stocks and bonds as markets respond to strong labor data and lower-than-expected wage growth. Consumer prices report due Thursday.
Read More
Mid-Week Market Minute 1.4.23
U.S. stocks are off to a slow start in the new year while international markets get a boost from encouraging inflation data. Important U.S. jobs report will be released Friday.
Read More
Market Recap – Week ending Dec. 30
The S&P 500 finished 2022 down 18.1%, its worst performance since 2008. The monthly employment report, the first key economic report of 2023, comes out Friday, Jan. 6.
Read More
Mid-Week Market Minute 12.28.22
With little change this week, the S&P 500 is on track for its worst year since 2008. Report shows climb in wholesale inventories, beating expectations. Home sales, jobs data due this week.
Read More
Market Recap – Week ending Dec. 23
The story for the U.S. economy this year has largely been about battling record-high inflation, which has left both equity and fixed income markets bumpier than a ride on Santa’s sleigh.
Read More
Mid-Week Market Minute 12.21.22
In response to higher interest rates, recessionary concerns persist. On the data front, November’s new home construction and permits continued to decline as borrowing costs continue to hamper affordability and demand.
Read More
Market Recap – Week ending Dec. 16
In the U.S., the S&P 500 index ended 2.1% lower as markets digested the news from the latest Federal Reserve meeting. The Fed delivered a 50bp (0.50%) rate hike for December and raised its projection for the peak Fed funds rate by 50bp to 5.00-5.25%.
Read More
Mid-Week Market Minute 12.14.22
The S&P 500 was more than 2% higher this week after CPI data showed headline inflation rose at a modest rate. A 50-basis-point rate hike is expected following the Fed meeting on Wednesday.
Read More
Market Recap – Week ending Dec. 9
Stock markets in the U.S. ended lower last week. The Fed is widely expected to slow the pace of rate hikes to 0.50% at this week’s meeting.
Read More
Mid-Week Market Minute 12.07.22
Stocks trended down the first half of the week. Ahead of December Fed meeting, inflation data (PPI, CPI) set for release Friday and next Tuesday, respectively.
Read More
Market Recap – Week ending Dec. 2
Major global markets saw stocks move higher. With the core PCE price index, a key inflation indicator, falling in November, Fed chair indicated a possible slowing of rate hikes.
Read More
Mid-Week Market Minute 11.30.22
S&P 500 rallied about 2% in November, overshadowed by the strong performance of international stocks. Friday will bring the widely followed jobs report for October.
Read More
Market Recap – Week ending Nov. 25
U.S. stocks traded higher in the holiday-shortened week. Key reports this week will provide clues to the status of inflation and the strength of the labor markets.
Read More
Mid-Week Market Minute 11.23.22
Stocks were higher in the holiday-shortened trading week. Investors will get a look at the durable goods report on Wednesday followed by the release of November’s FOMC meeting minutes.
Read More
Market Recap – Week ending Nov. 18
In the U.S., the S&P 500 index was down 0.6% for the week. While higher inflation might be pinching consumer wallets, recent economic data still point to a resilient consumer.
Read More
Mid-Week Market Minute 11.16.22
Recent inflation reports help quell inflationary fears as markets now are pricing in a 50-basis-point rate hike for December Fed meeting. Retail sales in October beat expectations.
Read More
Market Recap – Week ending Nov. 11
Consumer prices (CPI) were expected to increase 8.0% year-over-year, down from an 8.2% reading in September, but last week the U.S. saw its lowest level of headline inflation since January, a welcomed sign for investors.
Read More
Market Recap – Week ending Nov. 4
S&P 500 index was down 3.3% as investors brace for more interest-rate hikes following last week’s Federal Reserve meeting. Chairman Jerome Powell remarked it was “premature” to pause interest-rate hikes.
Read More
Mid-Week Market Minute 11.02.22
U.S. stocks traded higher on Wednesday as Wednesday’s Fed interest-rate increase was expected. Fed will watch strength of labor market, along with inflation and growth indicators.
Read More
Market Recap – Week ending Oct. 28
This week, markets will focus on the Federal Reserve meeting (Nov. 1-2) with Fed expected to raise rates 75 bp.
Read More
Financial Professional Year-End Tax Tips
Now that we’re in the fourth quarter, it’s the perfect time to schedule year-end tax conversations with your Financial Professional before the rush and demands of the holiday season consumes everyone’s time and focus.
Read More
Mid-Week Market Minute 10.26.22
Investors will keep an eye on third-quarter GDP data on Thursday, along with core PCE, and the University of Michigan’s consumer sentiment report on Friday.
Read More
Market Recap – Week Ending Oct 21
S&P 500 rose 4.8% on a solid start to the third-quarter earnings season last week, leading global stocks higher.
Read More
Mid-Week Market Minute 10.19.22
After corporate earnings beat expectations, stocks staged an impressive rally this week.
Read More
Market Recap – Week Ending Oct 14
The September Consumer Price Index (CPI) report showed headline inflation climbed 0.4% month-over-month, missing estimates for a more modest increase.
Read More
Mid-Week Market Minute 10.12.22
Thursday’s CPI report is arguably the most important individual piece of data between now and the next Federal Reserve meeting on November 2nd.
Read More
Market Recap – Week Ending Oct 7
This week, focus will be on the Thursday consumer price index (CPI) report, with headline inflation expected to fall to 8.1% for September, down from 8.3% in August.
Read More
Mid-Week Market Minute 10.05.22
The past few weeks serve as an important reminder that the best and worst days in the market often occur very close together.
Read More
Market Recap – Week Ending Sept 30
Although 4Q22 looks set to be another tough quarter for public markets, investors should not be overly pessimistic.
Read More
Mid-Week Market Minute 09.28.22
U.S. stocks were largely unchanged for the week as volatility spiked amid global economic concerns. Investors continue to grapple with the impacts of higher interest rates against the backdrop of slowing economic growth.
Read More
Market Recap – Week Ending Sept 23
Drops in the S&P 500, global and international stocks following last week's Fed rate hike are contributing to concerns over a global economic slowdown.
Read More
Mid-Week Market Minute 09.21.22
Against the backdrop of persistently high inflation, the Federal Reserve enacted its third consecutive 0.75% interest rate increase on Wednesday.
Read More
Market Recap – Week Ending Sept 16
Global stocks traded lower last week amid ongoing angst that central banks around the world will continue with aggressive monetary policy in raising interest rates to fight inflation.
Read More
Mid-Week Market Minute 09.14.22
Tuesday’s higher-than-expected inflation report caught markets off guard, implying a third consecutive 0.75% (75 basis point) rate hike at the next Fed meeting on Sept. 21.
Read More
Market Recap – Week Ending Sept 9
As economic growth slows this year, a key question for investors is whether job openings can fall from their historical highs without a substantial rise in unemployment.
Read More
Market Recap – Week Ending Sept 2
Global stocks were lower last week on the heels of strong U.S. employment and manufacturing data, as investor concerns continue over inflation and aggressive rate hikes by the Federal Reserve.
Read More
Mid-Week Market Minute 08.31.22
The Conference Board’s gauge of consumer confidence improved more than expected in August to a three-month high, while the Jobs Openings and Labor Turnover Survey (JOLTS) showed available positions unexpectedly increased to 11.2 million in July.
Read More
Market Recap – Week Ending August 26
Stocks in the U.S. traded sharply lower last week as investors became increasingly skeptical the Federal Reserve will be able to tame inflation without causing a significant slowdown in the economy.
Read More
Mid-Week Market Minute 08.24.22
Global stocks suffered ahead of this week’s key Fed symposium in Jackson Hole, Wyoming. The S&P 500 was lower by about 2% mid-week, with stocks in technology and communications sectors amongst the worst performers.
Read More
Market Recap – Week Ending August 19
As markets continue to focus on inflation, key events this week will be a speech from Federal Reserve Chair Jerome Powell on Friday at the Jackson Hole Economic Symposium, as investors look at interest-rate hikes and guidance for the rest of the year
Read More
Mid-Week Market Minute 08.17.22
Housing data continues to point toward signs of weakness. Housing starts in July fell a worse-than-expected 9.6% from June to mark its worst reading since February 2021. Building permits declined 1.3%, its slowest pace since September 2021.
Read More
Market Recap – Week Ending August 12
Following a relentless rise in inflation this year, markets finally have been able to breathe a sigh of relief as the July inflation figures were softer than expected.
Read More
Mid-Week Market Minute 08.10.22
Stocks rallied this week as investors digested the latest update on inflation. The Consumer Price Index (CPI) was unchanged during the month of July, against expectations for a 0.2% gain.
Read More
Market Recap – Week Ending August 5
A strong jobs report eased recession fears but suggested that the Fed will need to continue to raise short-term funds rates. Focus will be on the consumer prices (CPI) report due out on Wednesday.
Read More
Mid-Week Market Minute 08.03.22
Stocks were modestly lower in early trading this week as markets remained cautious amid heightened geopolitical tensions.
Read More
Market Recap – Week Ending July 29
The U.S. economy shrank by more than expected to -0.9% annualized for the second quarter of 2022, primarily on slowing investment and spending, along with a decrease in inventories.
Read More
Mid-Week Market Minute 07.27.22
As anticipated, the Federal Reserve enacted its second consecutive 0.75% interest-rate increase on Wednesday. Hikes in June and July represent the largest consecutive moves since the early 1990s.
Read More
Market Recap – Week Ending July 22
Global stocks ended last week in positive territory, as better-than-expected corporate earnings in the U.S. aided consumer optimism despite economic and interest-rate pressures.
Read More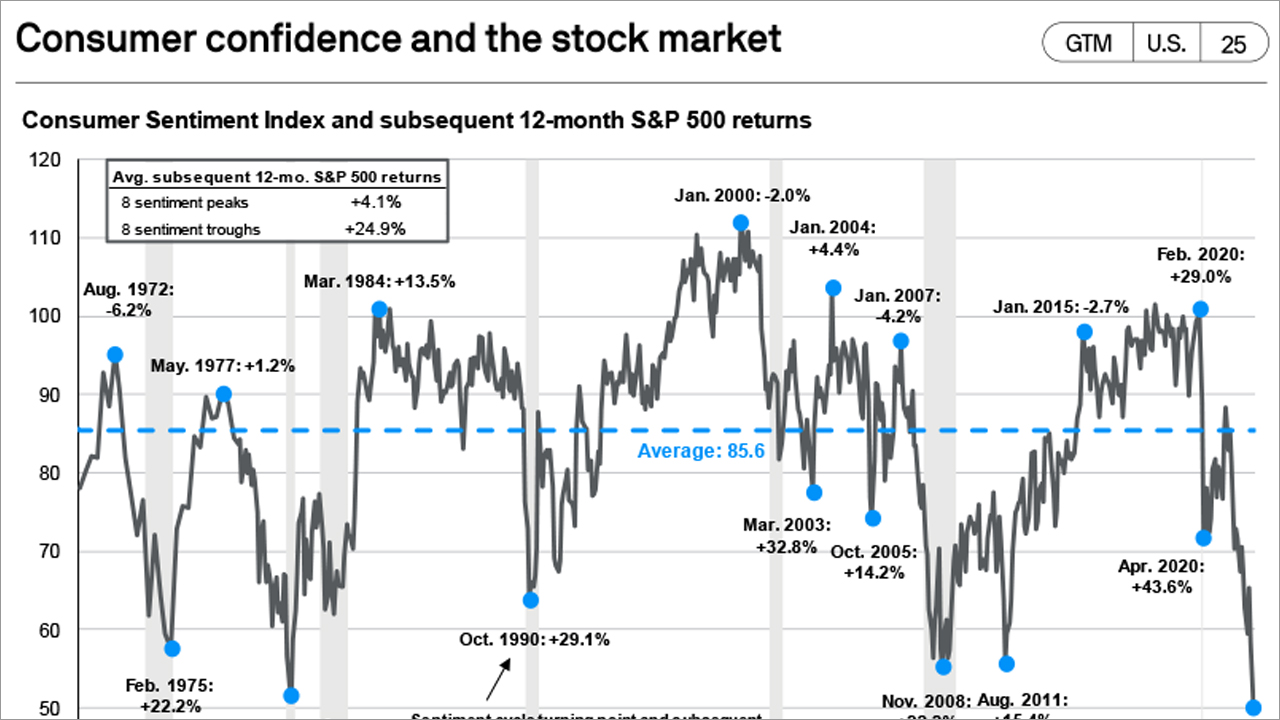
Consumer Confidence and the Stock Market
Don’t let how you feel about the economy overrule how you feel about investing.
Read More
Mid-Week Market Minute 07.20.22
Focus next week will be on the Federal Reserve meeting July 26-27, with markets now pricing in about a 70% chance of a 75 basis point (0.75%) rate hike and an expectation of an ending funds rate of around 3.5% by year-end.
Read More
Market Recap – Week Ending 07.15.22
Despite a strong rally on Friday, stocks traded in negative territory last week as higher-than-expected inflation data added to concerns about aggressive rate hikes by the Federal Reserve. In the U.S., the S&P 500 index fell 0.9%.
Read More
Mid-Week Market Minute 07.13.22
Stocks turned lower on Wednesday after the Consumer Price Index (CPI) report showed U.S. inflation accelerated in June by more than forecasted. The consumer price index rose 9.1% from a year earlier, the largest gain since the end of 1981.
Read More
Market Recap – Week Ending 07.08.22
Global stocks traded higher last week, led in the U.S. by the 2.1% return of the S&P 500 index. Despite expectations for ongoing tighter monetary policy, easing oil prices and some positive signs for economic growth helped stocks finish positive.
Read More
Mid-Week Market Minute 07.06.22
The Federal Open Market Committee (FOMC) has changed dramatically regarding transparency over the years, now disclosing policy changes at the end of each meeting. Historically, the Fed used to keep investors guessing about policy changes.
Read More
Market Recap – Week Ending 07.01.22
U.S. fixed income markets declined 10.3%, as the Federal Reserve hiked rates by 75 basis points at its June meeting in response to the higher-than-expected inflation. The core personal consumption (PCE price index) decreased to 4.7% annualized.
Read More
Mid-Week Market Minute 06.29.22
Revised data for first quarter GDP was reported on Wednesday morning, indicating the U.S. economy contracted at a 1.6% annual rate for the quarter. Weakness was primarily led by volatile trade and inventory data.
Read More
Market Recap – Week Ending 06.24.22
After three straight weeks of declines, stocks regained positive momentum last week. In the US, the S&P 500 index finished the week higher by 6.5%, as investors continue to monitor the effects of inflation and monetary policy on the economy.
Read More
Mid-Week Market Minute 06.22.22
Stocks rallied in early trading this week as markets continue to grapple with central bank policy and the ultimate repercussions for global economic growth.
Read More
Market Recap – Week Ending 06.17.22
Stocks were lower as central bank tightening amid persistent inflation and pricing pressures continued. In the U.S., the Federal Reserve raised the short-term funds rate last week by 75 basis points, the largest increase since 1994.
Read More
Mid-Week Market Minute 06.15.22
The Federal Reserve announced it would raise rates by 75 basis points, in line with the markets’ expectations. There was a tremendous amount of investor angst leading up to the meeting in the face of the highest inflation in decades.
Read More
Market Recap – Week Ending 06.10.22
Stock market volatility continued last week as investors digested an above-consensus inflation report and upcoming monetary tightening by the Federal Reserve.
Read More
Mid-Week Market Minute 06.08.22
Stocks edged higher in early trading this week despite increasing concerns surrounding a slowdown in global economic growth.
Read More
Market Recap - Week Ended June 3
Global stock returns were mixed last week as volatility continues in the markets. Emerging market stocks (MSCI EM) finished the week 1.8% higher, while in the U.S. the S&P 500 index was down 1.1% for the week.
Read More
Mid-Week Market Minute 06.01.22
Stocks were mostly higher this week as Wall Street turned the page on another volatile month. The S&P 500 edged out a positive total return of about 0.20% in May after briefly dipping into bear market territory.
Read More
Market Recap – Week Ending 05.27.22
U.S. stocks ended a seven-week stretch of declines last week as some positive retail earnings helped investor sentiment.
Read More
Mid-Week Market Minute 05.25.22
Stocks resumed their downward trajectory alongside elevated volatility as markets digested softer-than-expected data on the economic front.
Read More
Market Recap – Week ended May 20
Stocks were mixed across the world last week as investors evaluated softer consumer demand, persistent inflation, and slowing economic growth.
Read More
Mid-Week Market Minute 05.18.22
Stocks around the globe stabilized in early trading this week after weathering a steep sell-off last week, fueled by the ongoing uncertainty surrounding inflation and the future path of monetary policy.
Read More
Market Recap – Week Ending 05.13.22
Stocks across the globe were lower last week, as markets continue to be challenged by a global economic slowdown given the COVID-19 lockdowns in China, the Russia-Ukraine war, and persistent inflation.
Read More
Mid-Week Market Minute 05.11.22
Stocks in the U.S. traded sharply lower this week as inflationary pressures continued to mount. Overseas, international stocks fared slightly better, with China’s Shanghai index flat for the week.
Read More
Market Recap – Week Ending 05.06.22
Stocks vacillated last week as volatility remained elevated. In the U.S., investors evaluated guidance from the latest Federal Reserve meeting, while keeping an eye on corporate earnings and jobs data.
Read More
Mid-Week Market Minute 05.04.22
Stocks in the U.S. were about 2% higher for the week, with energy and utilities leading the way as the European Union’s proposed ban on Russian oil led to higher prices in global energy markets.
Read More
Market Recap – Week Ending 04.29.22
Stocks were lower in volatile trading last week as markets evaluated earnings, COVID-19 lockdowns in China, and Federal Reserve actions. In the U.S., the S&P 500 index was down 3.3% for the week as weak GDP ...
Read More
Mid-Week Market Minute 04.27.22
U.S. stocks sold off this week as the repricing in growth-related shares continued ahead of key earnings data. Markets remain vigilant as COVID-19 restrictions continue to weigh on China alongside looming central bank rate hikes.
Read More
Market Recap – Week Ending 04.22.22
Overview: Stocks fell across the globe last week on fears of faster rate hikes in the U.S. and renewed lockdowns from a recent COVID-19 surge in China. In the U.S., the S&P 500 index ended down 2.7%, and with the Hang Seng index in Hong Kong down ...
Read More
Mid-Week Market Minute 04.20.22
Global stocks rallied this week as investors digested corporate earnings reports alongside central bank commentary. Shares of Netflix (NFLX) plummeted on Tuesday following the company’s quarterly earnings report.
Read More
A Primer on Series I Savings Bonds
You may be familiar with Series E or EE savings bonds, which were the paper bonds you used to be able to buy at your local bank. Often used as gifts for birthdays or graduations, Series EE savings bonds earn a fixed rate of interest and ...
Read More
Market Recap – Week Ending 04.14.22
Stocks were lower last week as investors continue to monitor inflation and interest rates. Last week, markets digested two important inflation readings – the Consumer Price Index (CPI) and producer prices (PPI).
Read More
Mid-Week Market Minute 04.13.22
Global stocks took a breather this week as investors continued to monitor geopolitical and inflation risks. On Tuesday, data from the Bureau of Labor Statistics showed headline CPI rose by 8.5% from a year ago, the largest annual gain since 1981.
Read More
Market Recap – Week Ending 04.08.22
Stocks worldwide were lower last week, with the S&P 500 index down 1.2% on the week. In the U.S., investors focused on the release of the March FOMC meeting minutes, which indicated more aggressive monetary tightening from the Federal Reserve.
Read More
Mid-Week Market Minute 04.06.22
Global stocks retreated this week as markets grappled with a progressively more hawkish Federal Reserve along with a fresh round of European Union sanctions on Moscow.
Read More
Market Recap – Week Ending 04.01.22
International stock traded higher last week, led by emerging markets (MSCI EM) up 1.9%, and developed stocks (MSCI EAFE) trading 0.8% higher. In the U.S., the S&P 500 index was up a marginal 0.1%, as inflation concerns continued ...
Read More
Mid-Week Market Minute 03.30.22
Global stocks continued to mount an impressive rally this week as optimism surrounding ceasefire talks between Russia and Ukraine helped bolster sentiment.
Read More
Market Recap – Week Ending 03.25.22
Stocks across the globe were generally higher last week as geopolitical concerns continued to fuel volatility in the markets.
Read More
Mid-Week Market Minute 03.23.22
Global stocks moved higher in early trading this week as investors continue to take cues from the Federal Reserve while keeping a close watch on developments in Eastern Europe.
Read More
Market Recap – Week Ending 03.18.22
Stocks across the globe rallied last week as investors evaluated the latest Russia-Ukraine news and as the Federal Reserve began their cycle of interest rate increases.
Read More
Mid-Week Market Minute 03.16.22
Global stocks traded marginally higher this week as investors continue to assess the impacts of developments in Eastern Europe.
Read More
Market Recap – Week Ending 03.11.22
U.S. stocks and bonds fell last week as consumer prices (CPI) inflation reached a 40-year high and investors factored in the impact on global growth of Russia’s invasion of Ukraine.
Read More
Mid-Week Market Minute 03.09.22
Stocks traded solidly higher mid-week and recovered most of the losses from a sharp sell-off over the first two days of the week. The market’s main focus remains Russia/Ukraine as flows are being driven by possible progress toward a ceasefire deal...
Read More
Market Recap – Week Ending 03.04.22
The effects of the intensifying Russia-Ukraine conflict continued to drive global stocks lower last week. International stocks were hit the hardest, with international developed (MSCI EAFE) and emerging markets (MSCI EM) down 5.5% and 2.3%, ...
Read More
Mid-Week Market Minute 03.02.22
Global stocks moved lower this week amid the intensifying conflict between Russia and Ukraine. Russia’s invasion of Ukraine is sparking investor worries about supply shortages...
Read More
Market Recap – Week Ending 02.25.22
Global stocks sold off sharply mid-week as Russia invaded Ukraine, with uncertain ramifications causing investors to move to safe haven assets.
Read More
Market Turbulence – Rates and Russia
The return of market turbulence, heightened volatility, and geopolitical uncertainty have dominated the investment landscape as we begin the year 2022.
Read More
Mid-Week Market Minute 02.23.22
Stocks around the globe moved lower this week as investors assessed the impacts of the ongoing standoff between Russia and Ukraine.
Read More
Market Recap – Week Ending 02.18.22
Global stocks were lower last week as investors moved into safe assets amid rising tensions in Ukraine. The S&P 500 ended 1.5% lower, as geopolitical concerns dominated encouraging earnings releases.
Read More
Mid-Week Market Minute 02.16.22
Stocks around the globe were modestly higher in early trading this week. Improving COVID-19 trends and relatively upbeat earnings have provided a tailwind for risk assets despite looming inflation and geopolitical tensions.
Read More
Perspective on Late January Sell Off
Stocks in the U.S. continued to decline this week following three consecutive weeks of negative performance.
Read More
Roth Conversion – A Tax-Smart Retirement Strategy
If you’re approaching retirement, conventional wisdom recommends allowing your 401(k) savings to grow as long as possible to enjoy the benefits of compound growth at a tax-free rate.
Read More
Determining Retirement Plan Investment Allocation
Deciding how to invest your retirement plan balance can be difficult. Most retirement plans provide many investment options and choosing the best option for you can be challenging.
Read More
How to Handle the Death of a Loved One
Expected or not, managing issues that must be addressed following the death of a family member or friend can be extremely difficult.
Read More
Teach Children About Money Now, Or Be Ready to Help Later
Monetary transactions look much different today than they did 10, even 5, years ago. Today, consumers can pay for goods and services with a swipe of a card or through an app on a phone.
Read More
Tax Planning for the Biden Administration
Many individuals are stuck in a holding pattern as they wait to see what impact the Biden Administration will have on tax regulations.
Read More
Fee or Commission: What’s the Best Way to Pay Your Financial Advisor?
When looking for a financial advisor, there’s much to consider: what states they conduct business in, their certifications, whether you enjoy talking with them and trust them, what their specialties are, and, of course, how much they charge.
Read More
Investment Rules That Do Apply to Your Financial Advisor
Knowing what to watch for will help protect you. It’s, also, helpful for investors to know how to talk with their advisor. As they say, “knowing is half the battle.”
Read More
You’re an Accredited Investor: Now What?
Higher-income investors and those who have become millionaires—with seven-figure investment accounts, excluding their primary home’s value—become known as so-called “accredited investors.”
Read More
Should Your Financial Advisor Be Local?
There’s so much to consider when choosing a financial advisor: what kind of fees they charge, the services they provide, and whether you get along with them and trust them, to start. Should their location be in that list?
Read More
5 Solutions to the Biggest Financial Problems Families Face
Whether you make a lot of money or a little or have massive amounts of credit card debt or none, more than likely, finances are an issue in most households.
Read More
Financial Advisor Glossary: Common Financial Planning Terms
When you’re working with a financial advisor to plan your financial future, you’ll encounter a number of industry words and terms that might not be familiar to you.
Read More
5 Questions You Need to Ask Your Financial Advisor Before Buying a Home
Starting the homebuying process can be like taking a crash course in a different language, especially if you’ve never bought before.
Read More
Should I Diversify My Index Funds?
Consistent and responsible investing is all about diversity.
Read More
Should You Participate in an Employee Stock Purchase Plan?
An employee stock purchase plan (ESPP) can help employers promote loyalty among employees while allowing those same employees to participate in the success of the company they work for.
Read More
How to Review a Financial Advisor
Once you’ve found a financial advisor that you feel is a good match for your needs, what’s next? It’s a good idea to carefully review the person you’ll trust with your finances.
Read More
